Mobile devices increasingly function as wireless tracking beacons. Using the Bluetooth Low Energy (BLE) protocol, mobile devices such as smartphones and smartwatches continuously transmit beacons to inform passive listeners about device locations for applications such as digital contact tracing for COVID-19, and even finding lost devices.
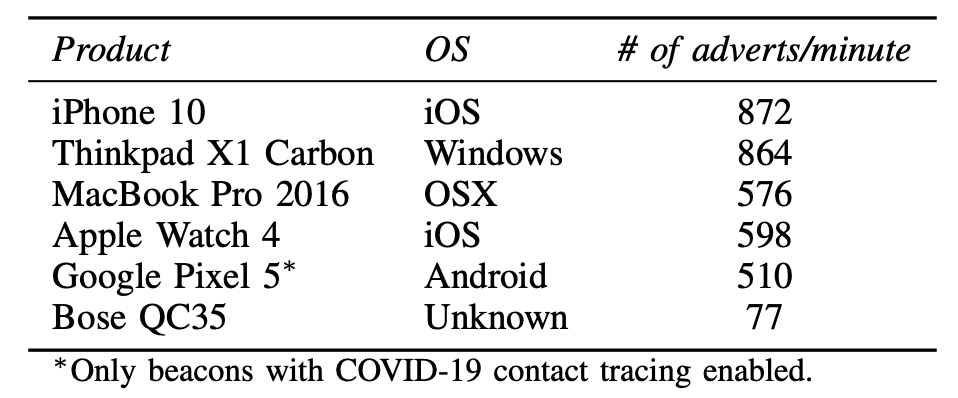
These applications use cryptographic anonymity that limit an adversary’s ability to use these beacons to stalk a user. However, attackers can bypass these defenses by fingerprinting the unique physical-layer imperfections in the transmissions of specific devices. The figure below shows examples of pysical-layer imperfections in WiFi/BLE combo chipsets.
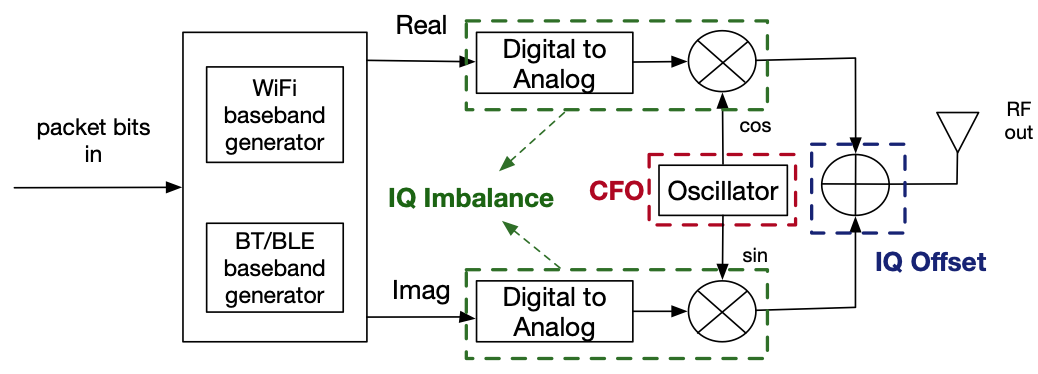
We build a tool to detect BLE signals and develop an algorithm to estimate these physical-layer imperfections accurately and create a profile for the target devices. An overal view of our BLE hardware imperfection estimation method is depicted below.
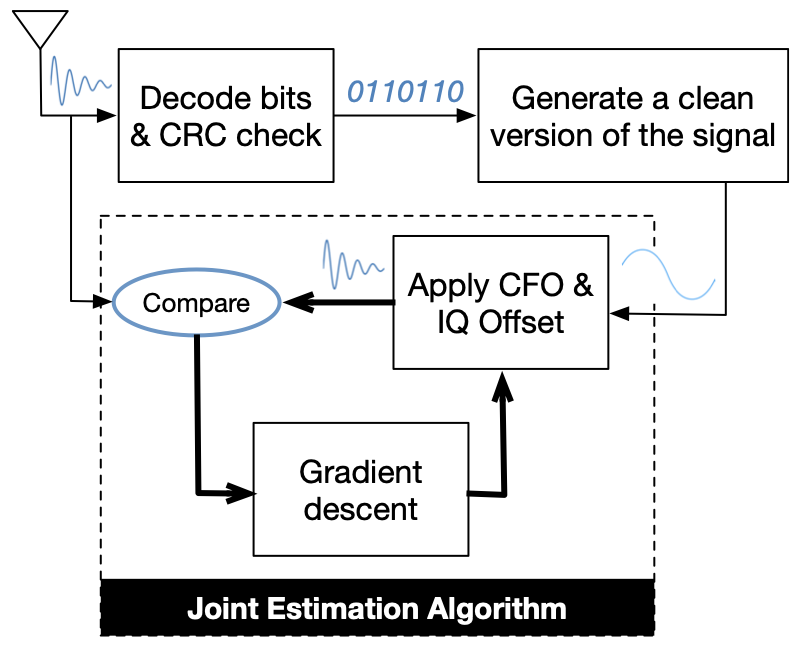
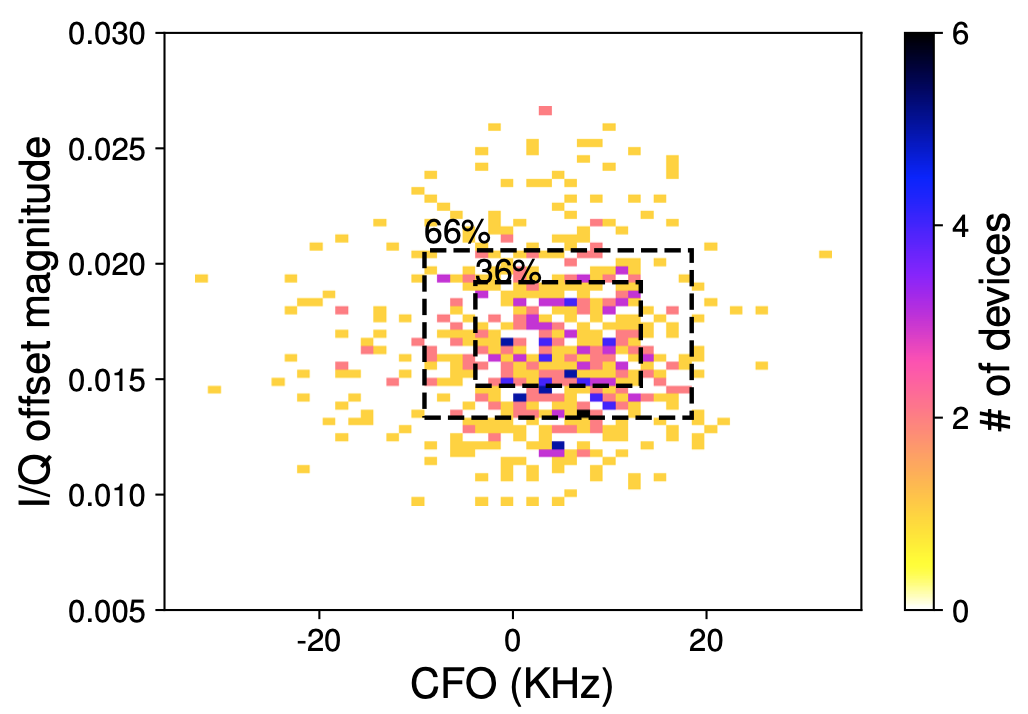
We further empirically demonstrate that there are several key challenges that can limit an attacker’s ability to find a stable physical layer identifier to uniquely identify mobile devices using BLE, including variations in the hardware design of BLE chipsets, transmission power levels, differences in thermal conditions, and limitations of inexpensive radios that can be widely deployed to capture raw physical-layer signals. We evaluated how much each of these factors limits accurate fingerprinting in a large-scale field study of hundreds of uncontrolled BLE devices, revealing that physical-layer identification is a viable, although sometimes unreliable, way for an attacker to track mobile devices. For example, the figure below shows histogram of imperfections across 647 BLE devices. ~50% of devices have unique imperfection fingerprints even amongst a large set of devices.
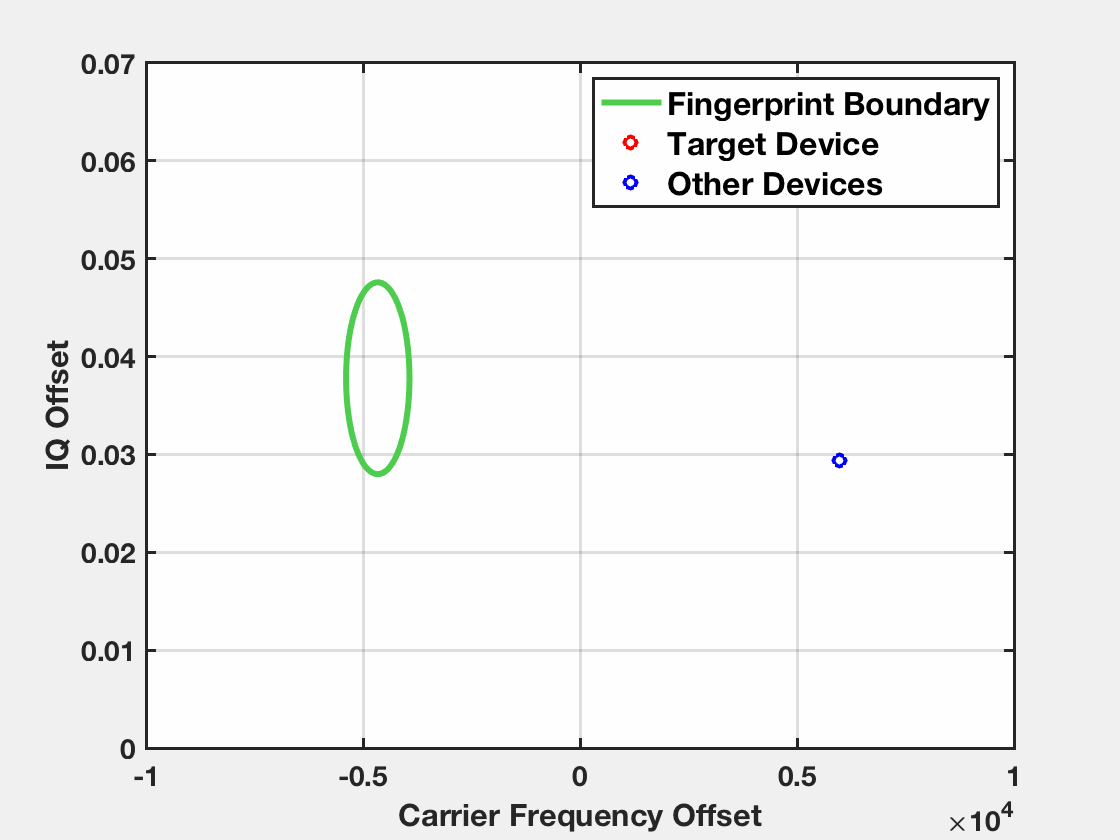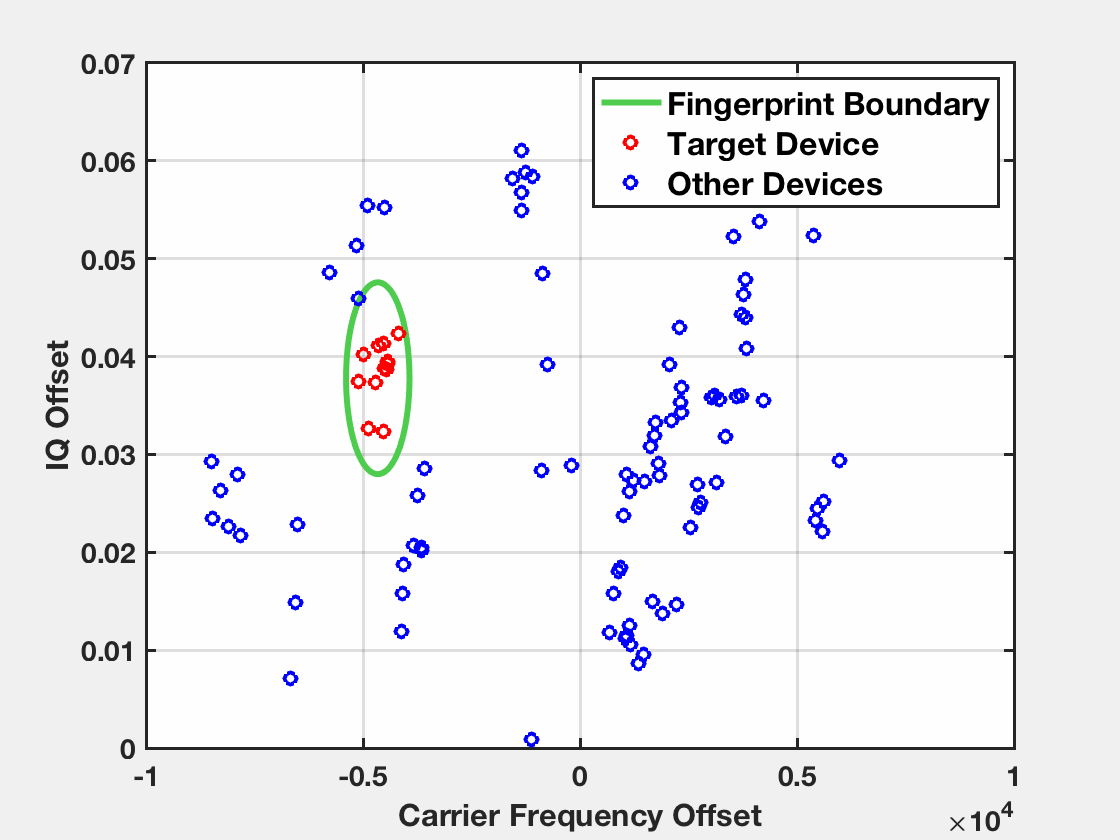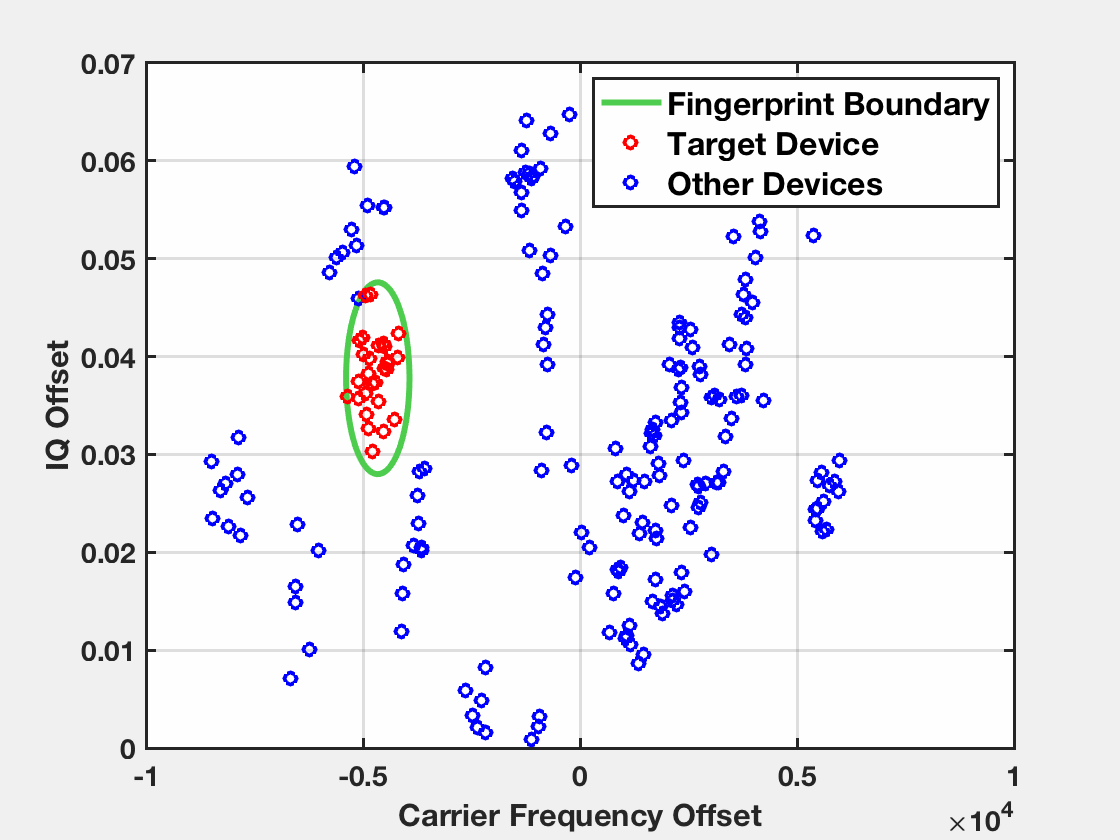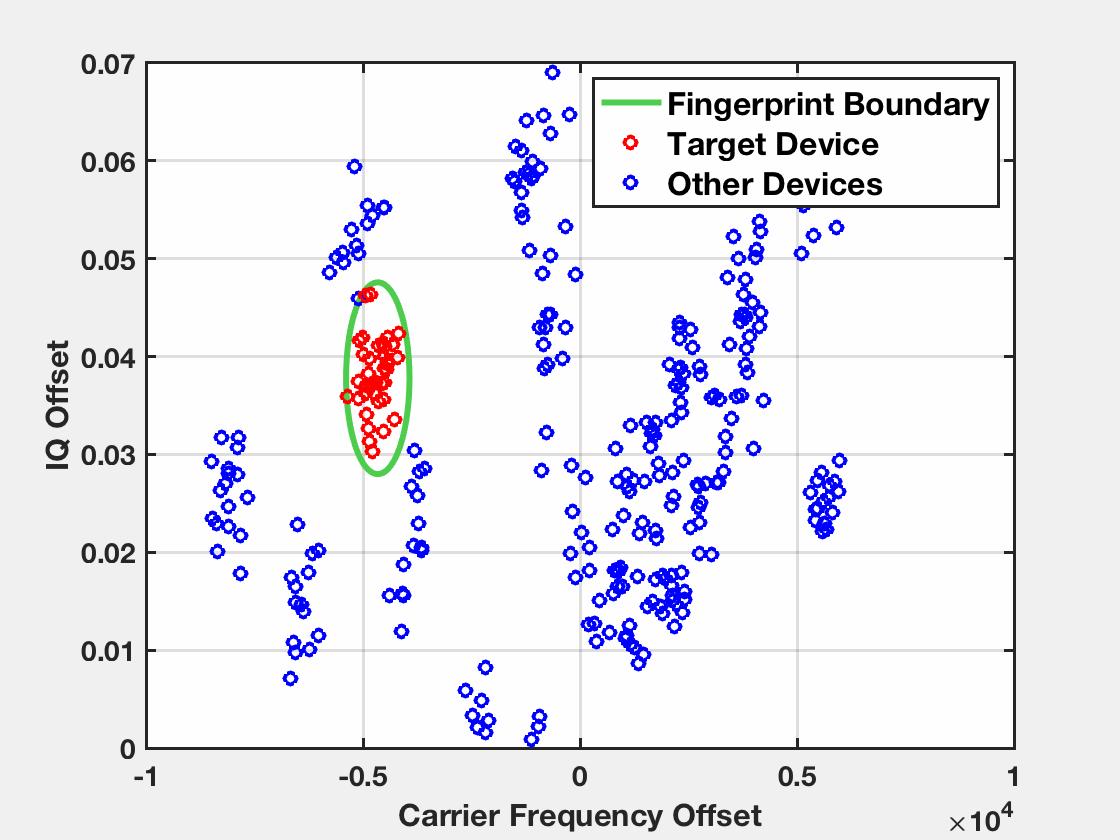
An example of an end-to-end attack is demonstrated below. The target device has been profiled before during the fingerprinting stage. The observed fingerprints of the target device during the identification stage fall inside the fingerprint boundary of the device while the fingerprints of other devices fall outside.